The SwiftKey keyboard flaw can allow an attacker to remotely access sensors (including features such as GPS, camera, and microphone); secretly install malicious app without the user knowing and fiddle with how other apps function, or how the smartphone works. The security flaw can also allow an attacker to eavesdrop on incoming/ outgoing messages or voice calls while can allow access to personal data such as images and text messages.
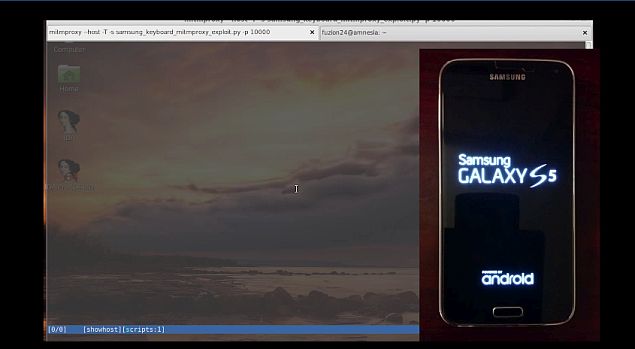 The flaw was discovered by NowSecure mobile security researcher Ryan Welton and was reported to Samsung in December last year. The company also claims that Computer Emergency Response Teams (CERT) was also notified about the security flaw “given the magnitude of the issue.”
The flaw was discovered by NowSecure mobile security researcher Ryan Welton and was reported to Samsung in December last year. The company also claims that Computer Emergency Response Teams (CERT) was also notified about the security flaw “given the magnitude of the issue.”
The mobile security company suggests that Samsung started providing a patch to mobile network operators in early 2015; though it is unknown whether the carriers released the patch to the devices on their network.
Detailing how an attacker could access the vulnerability, NowSecure notes, “The attack vector for this vulnerability requires an attacker capable of modifying upstream traffic. The vulnerability is triggered automatically (no human interaction) on reboot as well as randomly when the application decides to update. This can include geographically proximate attacks such as rogue Wi-Fi access points or cellular base stations, or attacks from local users on a network, including ARP poisoning. Fully remote attacks are also feasible via DNS Hijacking, packet injection, a rogue router or ISP, etc.”
In the meanwhile, SwiftKey in a emailed statement to NDTV Gadgets defended itself, saying the SwiftKey app available on Google Play and App Store has no such security flaw.
The company added that while SwiftKey supplies Samsung with the ‘core technology’ to power word predictions on its keyboards, it “appears the way this technology was integrated on Samsung devices introduced the security vulnerability.” SwiftKey said it is working with “long-time partner” Samsung to resolve the issue.
The statement added that the vulnerability is difficult to exploit, and only possible if the Samsung device user is connected to a compromised network (such as a spoofed public Wi-Fi network) and the device is undergoing a language update at the same time. The hacker would also require the right tools specifically intended to gain access to the device.
NowSecure suggests users can avoid insecure Wi-Fi networks, use a different mobile device, or contact carriers for patch information and timing, to negate the risks.







