On Android platform, each app has to go through a verification process where Google analyses it for virus and malware with the help of its security solution called Verify Apps. As a standard procedure, Verify Apps actively scans for the Potentially Harmful Apps (PHA) on the device, but what happens when it stops working? There could be a number of reasons behind it and Google has explained them along with the solution where it deploys various methods to identify security-related reasons behind your device not verifying apps.
On its Developers blog on Tuesday, Google detailed how it performs in such a situation where device is not checking with Verify Apps for security verifications of the apps. In such cases, there could be non-security reasons like buying a fresh mobile phone, but for more-concerning security-related reasons, Google steps in with its solutions to determine the exact cause. As per Google, when a device stops checking up with Verify Apps, it falls under the category of considered Dead or Insecure (DOI) devices.
“An app with a high enough percentage of DOI devices downloading it, is considered a DOI app. We use the DOI metric, along with the other security systems to help determine if an app is a PHA to protect Android users,” reads the blog, which further explains how Google segregates between potentially insecure apps and devices. Additionally, when Google discovers any vulnerabilities, a patch for Android devices is released with the security update system.
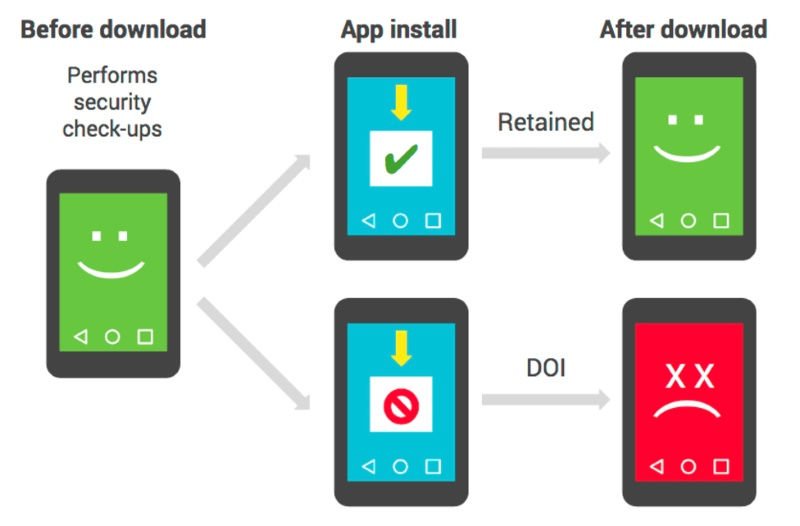
The process of flagging a DOI app is more of a mathematical equation where a certain score decides if that particular app is DOI or not. The Android Security team has to correlate the app install attempts and DOI devices to find apps that harm the device in order to protect the users. If a device keeps reporting app installs and their verification through Verify Apps, it is said to be ‘retained’ and considered safe thereafter. But if a device doesn’t do that, it’s considered potentially dead or insecure (DOI).
Google mentioned that ‘an app’s retention rate is the percentage of all retained devices that downloaded the app in one day.’ Considering retention as a strong indicator of device’s health, Google tries to maximise that in all possible ways. And for that, Google follows a DOI scorer, which takes the value as assumption that all apps should have a similar device retention rate.
The app retention rate is calculated using the following formula, where Z is the DOI score, N is number of devices that downloaded the app, x represents number of retained devices that downloaded the app, and p stands for the probability of a device downloading any app will be retained.

In Google’s words, “If an app’s retention rate is a couple of standard deviations lower than average, the DOI scorer flags it.” It further explains that “the DOI score indicates an app has a statistically significant lower retention rate if the Z-score is much less than -3.7. This means that if the null hypothesis is true, there is much less than a 0.01% chance the magnitude of the Z-score being as high. In this case, the null hypothesis means the app accidentally correlated with lower retention rate independent of what the app does.”
After the DOI score calculation, Google comes into action to bring offending apps to the top of DOI list. Following that, Google uses Verify Apps to remove existing installs of the app and prevent future installs of the app. The company added to this saying that is has used this method to identify apps that contained Hummingbird, Ghost Posh, and Gooligan malware. Affected devices are usually factory reset or permanently abandoned. This helps Google to discover PHAs and block them before they go on a spree to kill further Android devices.
Without this rigorous process, Google said it may have missed many apps that should otherwise have been suppressed. Google has shared that over 25,000 apps have been identified using this method.
[Source:- gadgets360]