Less than 24 hours after Google unveiled a Chrome extension that warns when user account passwords get phished, a security researcher has devised a drop-dead simple exploit that bypasses it.
This benign proof-of-concept exploit looks almost identical to a Google login page, and is typical of a malicious phishing page that attempts to trick people into entering their user name and password. If Google’s freely available Password Alert extension was better designed, it would provide a warning as soon as someone tried to log into the page with their Google password. Instead, the warning is completely suppressed. (Note: although Ars fully trusts the researcher, readers are strongly advised not to enter passwords for Google accounts they use for anything other than testing purposes.) A video of the bypass exploit is here
“It beggars belief,” Paul Moore, an information security consultant at UK-based Urity Group who wrote the exploit, told Ars. “The suggestion that it offers any real level of protection is laughable.” He went on to say Google would do better devoting its resources to supporting the use of password managers, since most of them provide much more effective protections against phishing attacks.
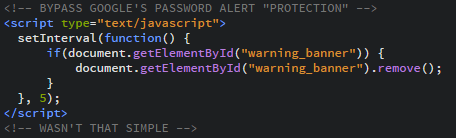
The bypass requires the following few lines of code:
<!-- BYPASS GOOGLE'S PASSWORD ALERT "PROTECTION" -->
<script type="text/javascript">
setInterval(function() {
if(document.getElementById("warning_banner")) {
document.getElementById("warning_banner").remove();
}
}, 5);
<script>
In an e-mail to Ars, Moore wrote:
Lines 2 & 8 are the start & end of a Javascript block.
Lines 3 & 7 (setinterval) tells the UA to carry out what’s inside the function every x milliseconds (5 in this case).
Line 4 checks to see if the warning_banner (the window which the Password Alert plugin creates when it finds a phishing site) exists. This line isn’t strictly necessary, but to hide any errors which may alert the user, it’s included.
Line 5 searches the DOM for an element with an ID of “warning_banner” and removes it.
Basically, the script runs every 5 milliseconds, searches the page for instances of Google’s warning screen and simply removes it. That’s it. Technically, the warning window still appears… but it disappears so quickly, the user wouldn’t know.
It wouldn’t be surprising to see Google update Password Alert to thwart Moore’s bypass. Still, his point about password managers stands.
Update: Google engineer Drew Hintz said Password Alert has been updated to version 1.4 to prevent Moore’s bypass from working. To install the new version, go to chrome://extensions/, enable developer mode, and click update extensions now.
[ Source :- Arstechnica ]







